Navigation Underground Space
The Era of Technological Innovation
The Era of Technological Innovation

Innovation driven · Deep cultivation of the soil
Building the future together
AI-Agent · Leading the Future
Focusing on the integrated digital twin technology of LLM big language model and artificial intelligence, deeply cultivating the research and application of intelligent solutions.
By providing professional services and innovative technologies, we bring efficient, precise, and secure solutions to various industries, helping customers achieve digital transformation and upgrading.
LLM+RAG
Intelligent Well Failure Response
& Decision Support Agent
LLM+MCP
AI-Enabled Reservoir Simulation
Transformation Agent
LLM+RPA
Universal Process Automation Agent
Intelligent recommendation of similar oil reservoirs (precise reuse of historical experience in solution development) and intelligent recommendation of drilling fluid design (dynamic optimization of fluid systems during drilling).
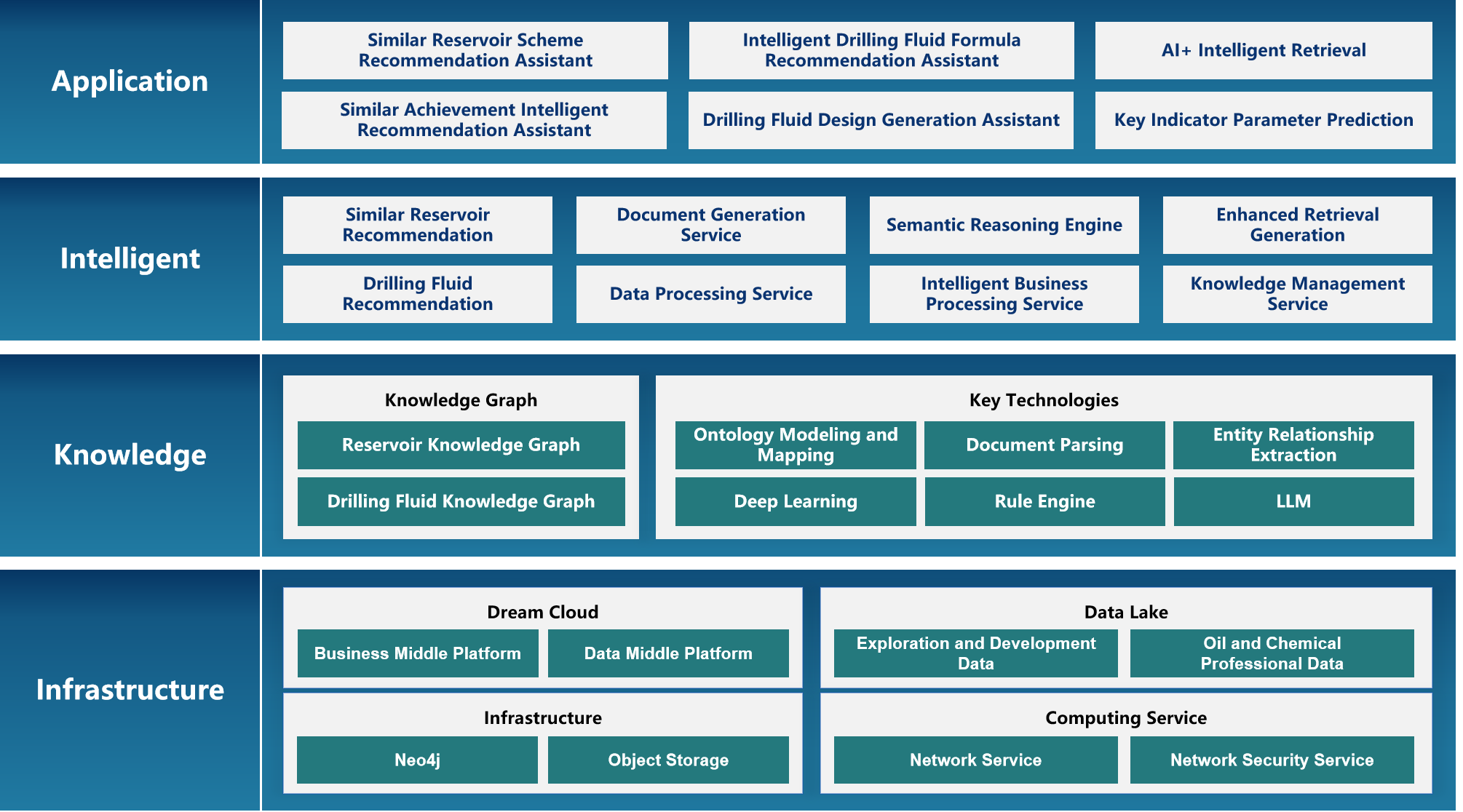
Build an oilfield AI architecture with "knowledge graph+big model" as the core, structure expert experience into knowledge, and achieve intelligent design and decision support through data-driven and intelligent generation methods.
Intelligent agent for automatic formulation of drilling fluid
Based on the knowledge graph, a structured precipitation of geological characteristics and engineering parameters of oil reservoirs is constructed, combined with the reasoning ability of complex scenarios in large models, to build a "knowledge driven+dynamic evolution" similar oil reservoir recommendation system, realizing the transformation of development experience from "expert experience" to "digital assets" and reuse mode from "artificial fuzzy matching" to "intelligent precise calculation".
Support dynamic knowledge update mechanism, multi-dimensional similarity calculation, cross regional knowledge transfer, etc. Through the mapping and transformation of knowledge graphs, achieve the sharing and reuse of oilfield knowledge in different regions.
Best ROI: Balance performance and cost through LLM Hub: Resource Dynamic.
Agile AI: Quickly respond to business requirements & scenarios by Agent Hub, which is designed with Matrix-style modular and multi-agent collaboration.
Know-How: Industry-specific large models and industry experience.
The Artificial INTELLIGENCE Solution
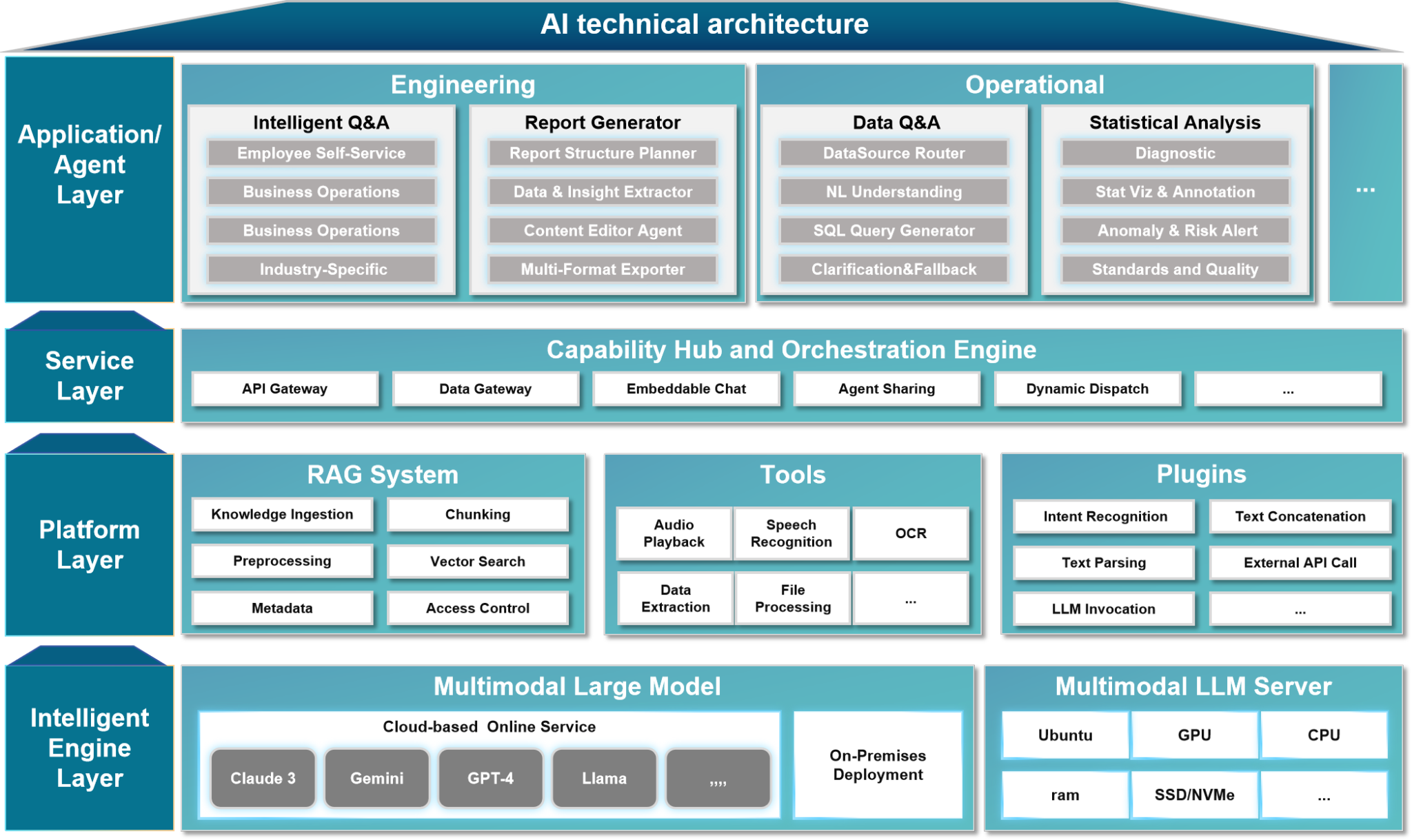
The platform adopts a four-layer architecture design:
1. Application Layer delivers scenario-based intelligent applications such as intelligent Q&A, data analysis, and report generation to users;
2. Service Layer provides capability dispatch and process orchestration hub for cross-system service collaboration;
3. Intelligent Platform Layer builds RAG systems, tools, and plugins supporting upper-layer flexible expansion;
4. Basic Environment Layer relies on multimodal large models and high-performance computing foundations to provide cognitive intelligence engines for the entire platform.
The synergy of these four layers creates a closed loop of "perception-understanding-decision-execution", comprehensively empowering the intelligent upgrade of industrial enterprises.

Based on advanced digital twin concepts, combined with advanced technologies such as the Internet of Things, big data analysis, and artificial intelligence.
We provide a comprehensive, accurate, and real-time digital management solution for key processes such as oil exploration, development, production, and management.
Wellbore-Reservoir AI Agent Platform
By creating intelligent agents, the platform can automatically operate various industrial software functional modules such as earthquake interpretation, geological modeling, and reservoir numerical simulation, effectively breaking down data barriers between different industrial software and allowing data to flow freely in each link, greatly improving work efficiency.
At the same time, the contour map automatically generated by the platform can dynamically display the correlation and degree of relevance between injection wells and production wells, providing intuitive and accurate data support for reservoir development decisions.
Industrial Applications · Technological Exploration
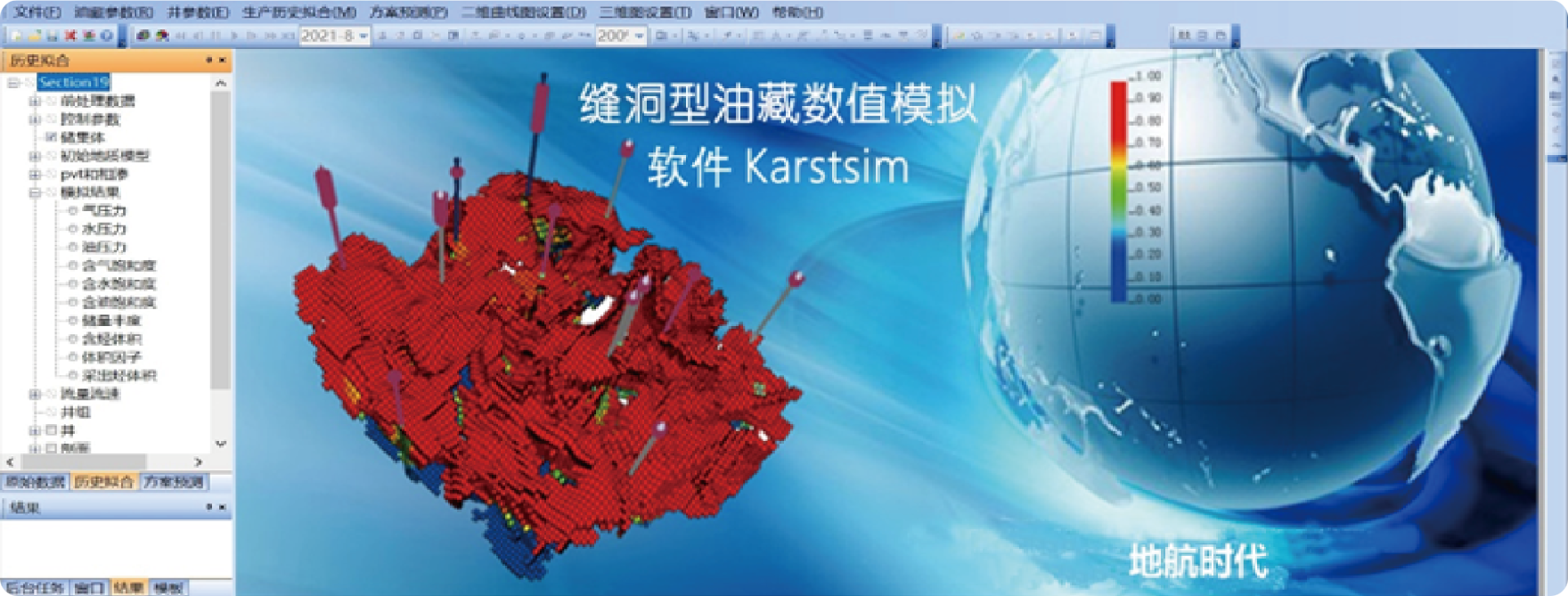
A lightweight reservoir simulation software optimized specifically for oil production company on well group simulation , automatically obtain real-time production data pushed by the platforms, and automatically adjust prediction models to ensure the accuracy and timeliness of predictions.
It supports the job card calling mode for intelligent agents without clicking on the software interface, following the OSGC reservoir industry standards.
Reservoir Simulation Software
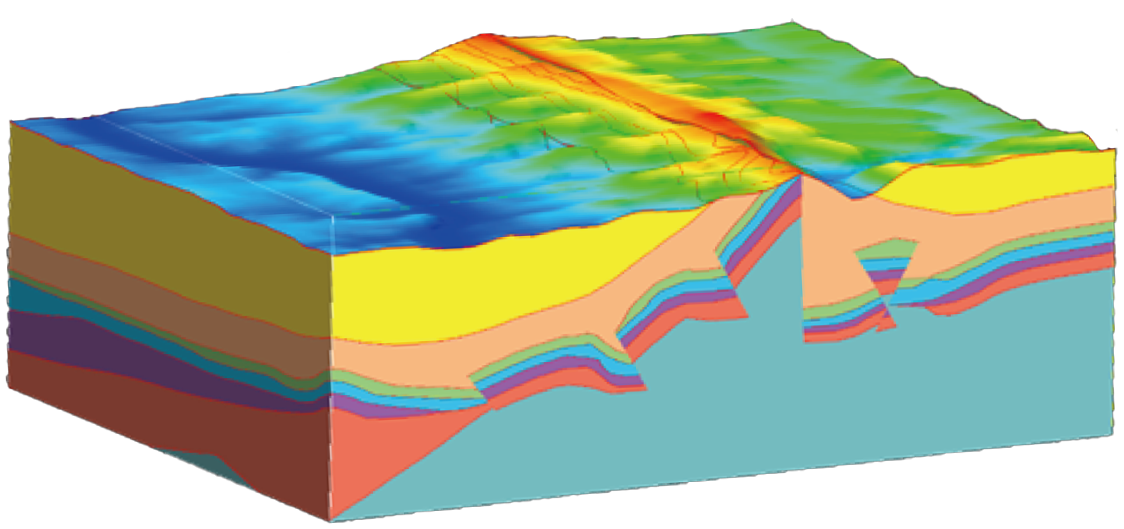
Geological Modeling Software
The core function of the geological modeling software is to achieve process-oriented modeling for different geological targets through a workflow manager, including the establishment of horizon models, fault surface models, structural models, and attribute model.
It also supports the construction of basin geological models on a billion-level scale, enabling modular invocation by geological modeling intelligent agents to achieve personalized modeling customized for geologists without the need for software interface operations.
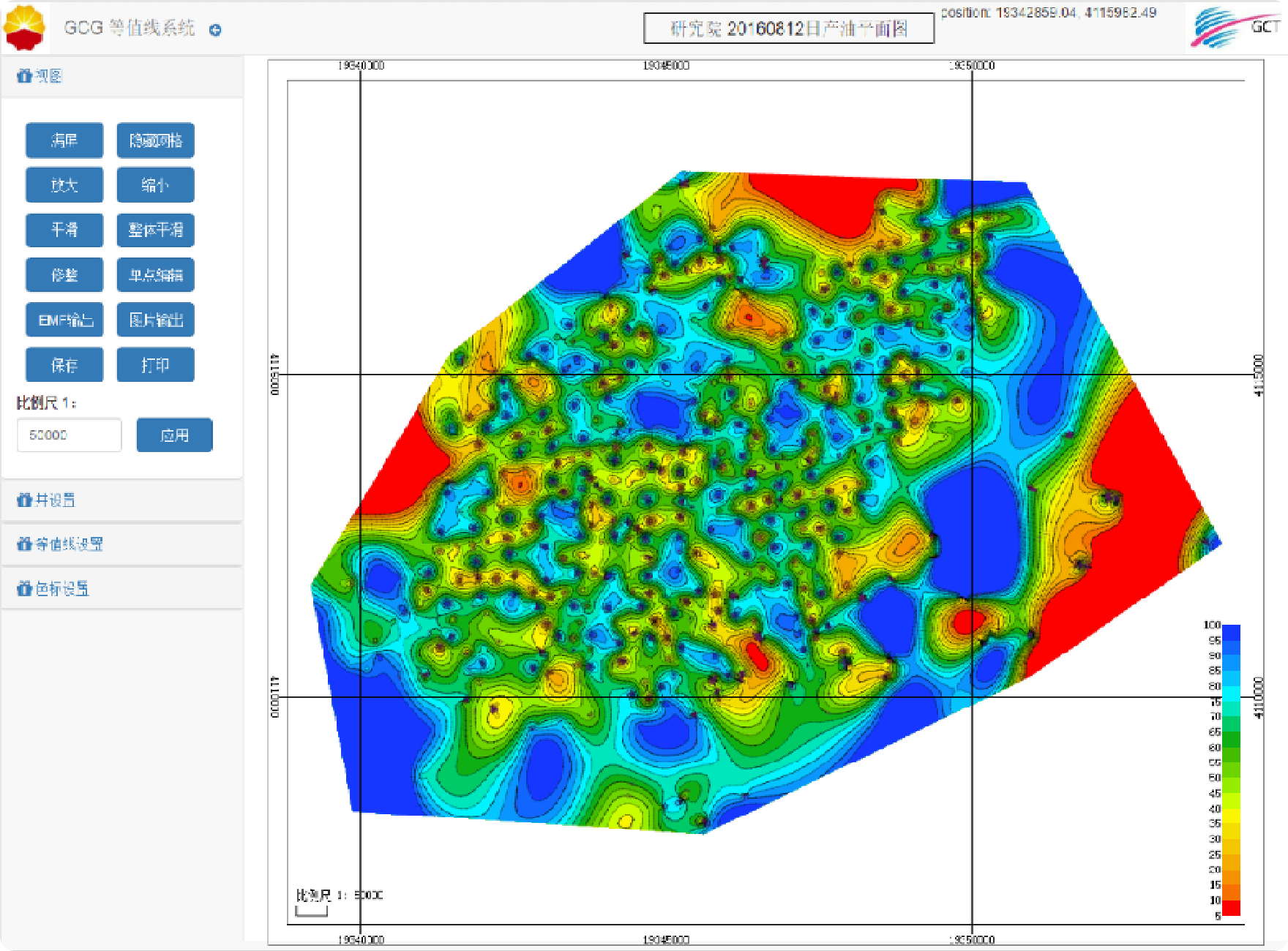
Mapping based on web contour lines
Designed using the B/S framework and developed based on HTML5 web technology, the underlying layer uses the PetroChina A2 database.
Users do not need to install any plugins and can generate contour maps (in vector format) on the web page.
Five methods for generating contour lines are provided, and any one can be selected for drawing
Nearest Neighbor Method, Minimum surface method, Minimum curvature method, Radial basis function method, Steady Trend Method.
Intelligent Data Query and Mapping
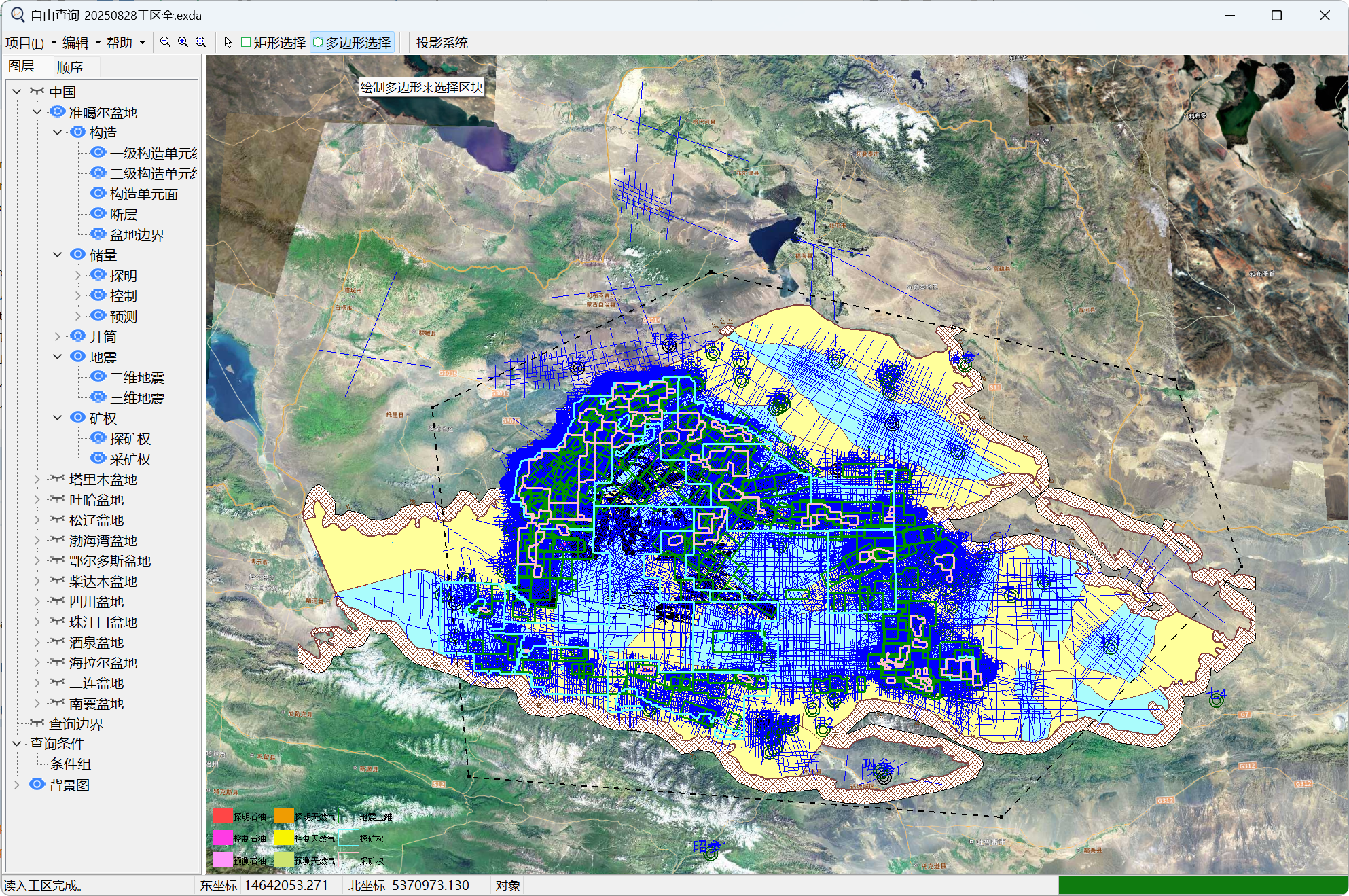
Based on the C++VCL framework and OLE object connection and embedding technology, a local database is formed using Excel data.
Users can achieve two-dimensional display of reserves, wells, earthquakes, mining rights, faults and other data, as well as quickly select ranges based on graphics to achieve data queries.

EasyCore - Description Software
EasyCore has the universal plotting function of any core description software, as well as unique display features and beautiful visualization functions. It is suitable for Windows operating systems and tablets, and can save logging data in various digital forms for easy data analysis and sharing.

EasyCopy - 2D graphics processing
EasyCopy utilizes the latest ergonomic interface to process various types of graphic data.
Worktile provides rich drawing tools, such as drawing tools for basic shapes such as lines, curves, rectangles, circles, polygons, etc., which can meet users' needs for drawing and editing various 2D shapes.
Worktile provides rich drawing tools, such as drawing tools for basic shapes such as lines, curves, rectangles, circles, polygons, etc., which can meet users' needs for drawing and editing various 2D shapes.

EasyDB - Core Description and Interpretation Results Database
It can achieve centralized management, query, display, and analysis of core data. Adopting optimized data structures, supporting multiple data types, ensuring efficient storage and reading performance, it can quickly store, retrieve, and update core description and interpretation results data, reduce data processing time, and improve work efficiency.

Opendtect - High frequency sequence stratigraphy interpretation system
A guide body can be directly generated, which contains the inclination and azimuth information of each sampling point in space. When processing and filtering multiple attributes, the use of guidance bodies fully considers the spatial distribution of geological targets, thereby improving the accuracy of target body and fault detection, and more accurately identifying and tracking the boundaries and morphology of geological bodies.
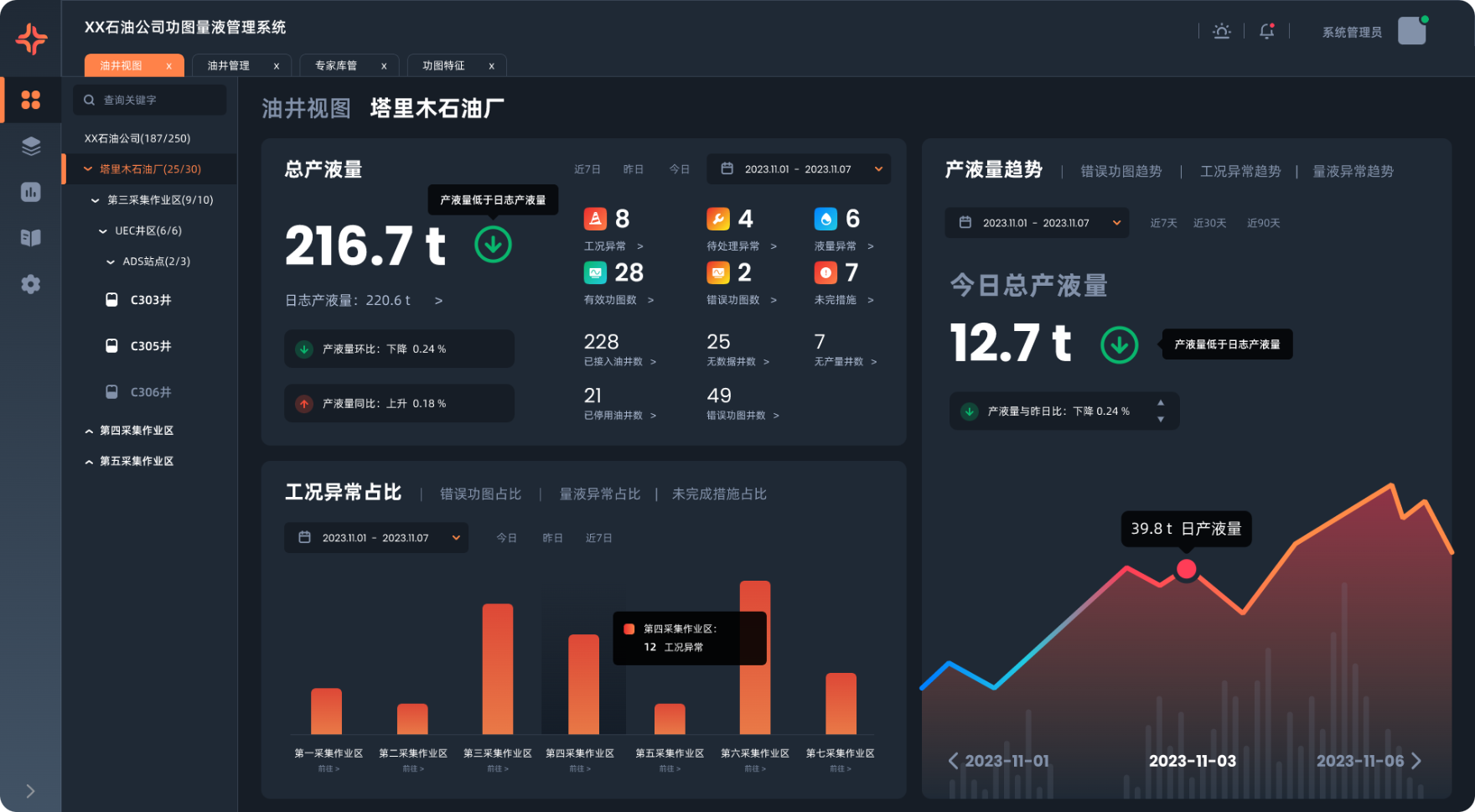
Digital Butler Service
It realizes functions such as intelligent production monitoring at the well site, intelligent working condition diagnosis, intelligent production early warning, intelligent measure push and intelligent output forecast, and achieves real-time production optimization and overall efficiency improvement at the well site.
Smart Oil and Water Wells
Application Scenario
Realize the integrated process management of unified monitoring of on-site production well management, abnormal condition diagnosis and problem handling.
Application Value
Create an intelligent well site integrated management and control platform to achieve unified management of real-time production parameters, videos and equipment maintenance of production wells, realize intelligent analysis of abnormal conditions and abnormal production of production wells, and improve well site management efficiency and cost.
Application Value
Create an intelligent well site integrated management and control platform to achieve unified management of real-time production parameters, videos and equipment maintenance of production wells, realize intelligent analysis of abnormal conditions and abnormal production of production wells, and improve well site management efficiency and cost.
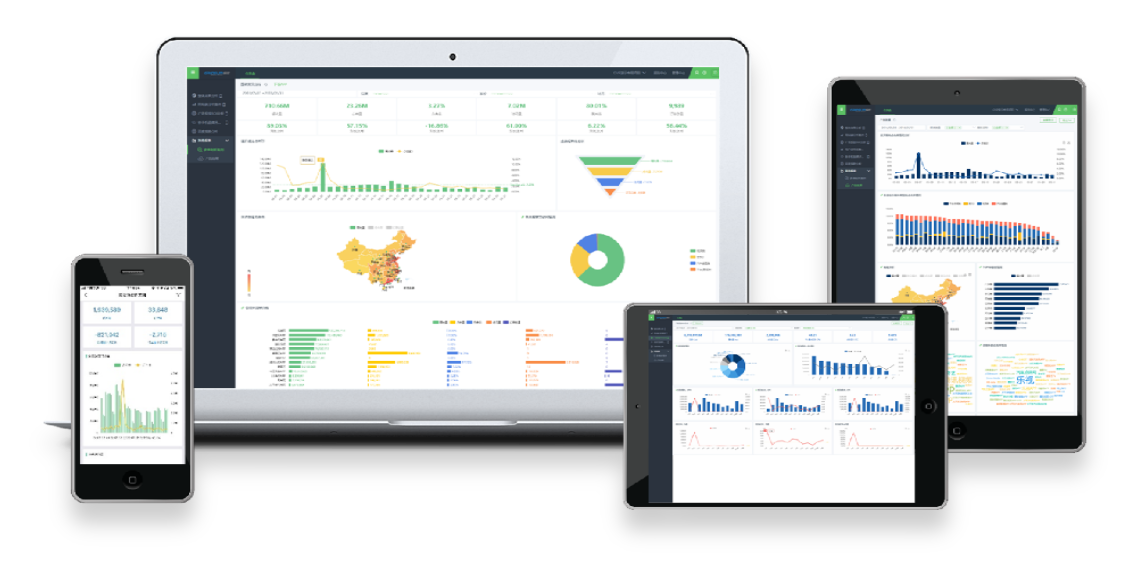
Cloud based Production Monitoring System: Based on relevant tool components, it is a one click comprehensive information query and display system for business objects such as wells, ground, and organizational structures. Users can customize and select the desired content to view.
Based on custom front-end configuration, suitable for display on PC, PAD, and various mobile devices.
SCADA Unified Configuration Platform
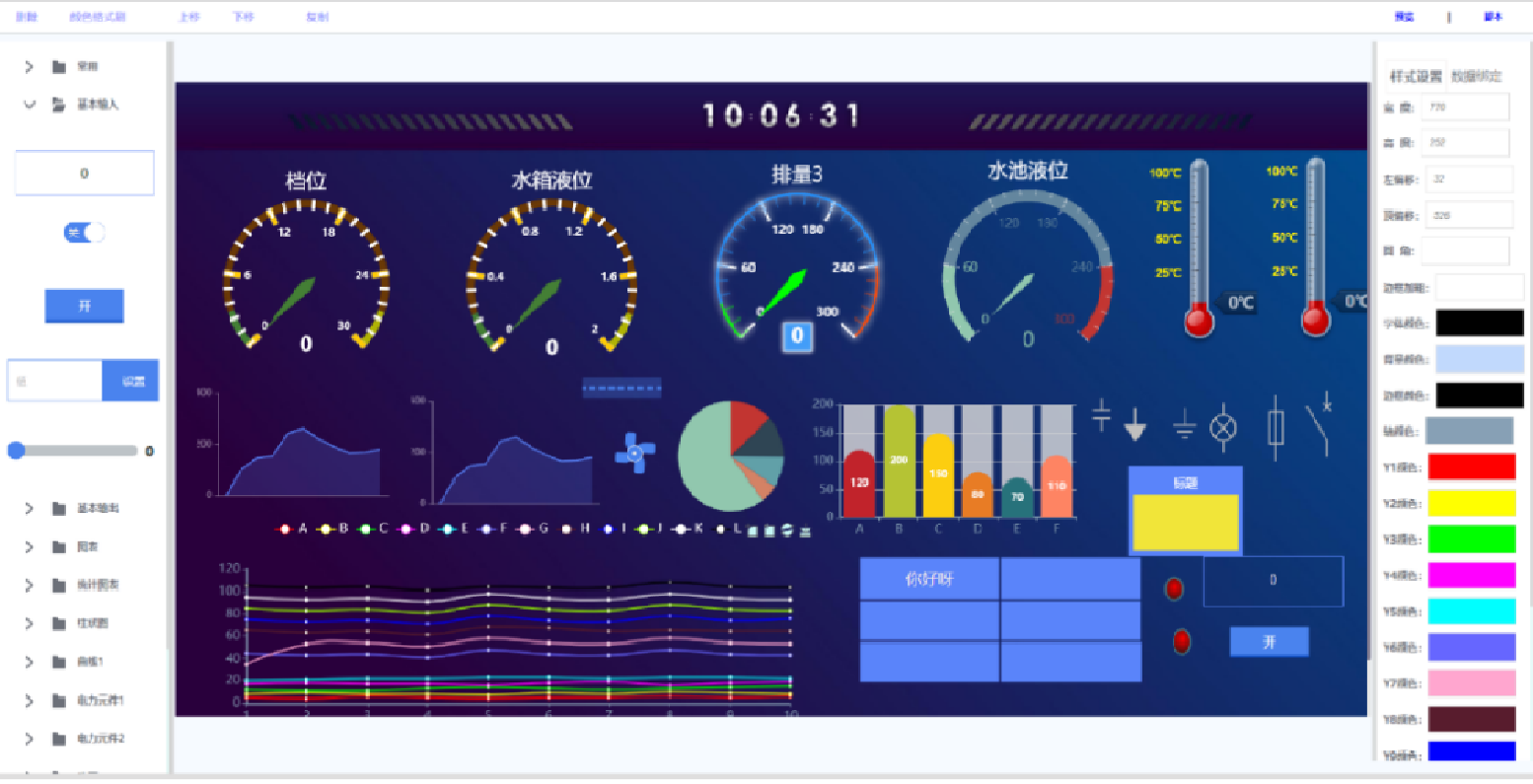
Advantages of Cloud SCADA System
Provide rich containers, graphics, and visualization components.
A flexible and easy-to-use flowchart editor that allows users to independently develop the process flow interface by dragging and dropping on a web page without the need for code.
A flexible and easy-to-use flowchart editor that allows users to independently develop the process flow interface by dragging and dropping on a web page without the need for code.
Reduce personnel cost cycle and effectively protect the core technology of the enterprise.
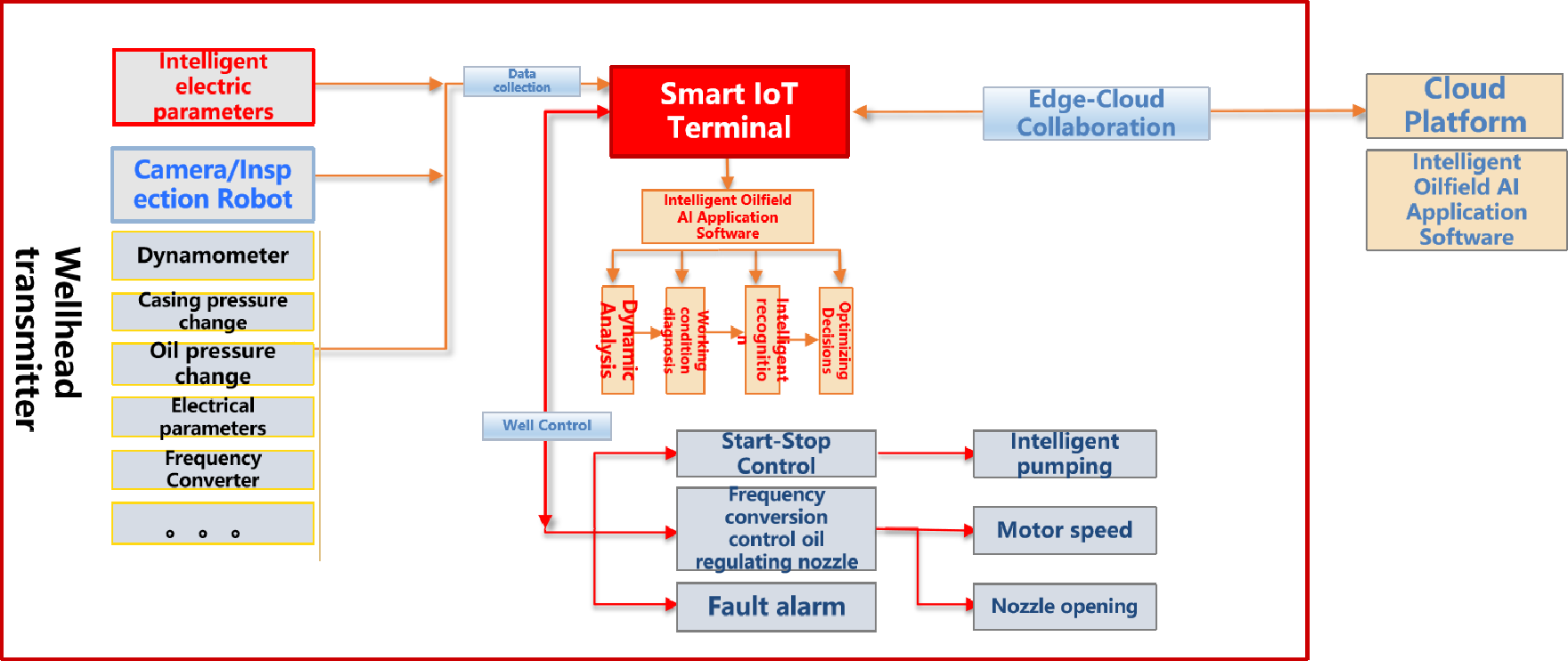
Single well measurement and control: single well data acquisition + high-frequency electrical parameter sampling + motor control.
Edge computing: built-in 4-core processor/1TOPS high-speed computing power + 32G large-capacity hard disk storage; provides 1-way video access and intelligent identification.
Intelligent application: self-developed edge computing application framework, which can deploy a variety of intelligent application software (APP) in a containerized manner, and can locally realize advanced functions such as single well working condition diagnosis, power diagram measurement, intelligent identification, and collaborative control.
Intelligent vision: with 4-channel high-definition video encoding/decoding processing capabilities; realize on-site visual intelligent identification of 1-channel high-definition video; on-site visual real-time collaboration of wellhead control; on-site control and video processing of inspection robots.
Communication gateway: built-in Zigbee, Wi-Fi and other wireless communication modules are optional; with 26 I/O interfaces; supports 1 optical fiber, 2 high-speed network ports, 4G/5G wireless and other communication modes.
Edge Computing Intelligent IoT control terminal
Data Security & IOT Devices
GEOCRUISER products cover multiple business areas such as drone technology, geological exploration, and intelligent surveying.
These products not only represent the profound technological research and development capabilities of the aviation industry, but also bring unprecedented changes and improvements to related industries.
At the same time, CATL is also Huawei's designated distributor for hardware equipment in the central and southern regions of PetroChina.

isRTU Integrated Safety RTU
RTU (Remote Terminal Unit) is a remote measurement and control unit device responsible for monitoring and controlling on-site signals and industrial equipment.
Due to its long communication distance, use in......

Next generation firewall
Establish secure access and protection mechanisms for boundaries
The next generation firewall can recognize application layer protocols and perform access control based on application types, which is more precise than traditional firewalls that rely on quintuples for access control. It also meets the boundary protection requirements of Equal Protection 2.0.

Industrial firewall
Establish a secure access mechanism for industrial network area boundaries
Industrial firewall is based on traditional firewall functions, adding recognition and deep parsing of industrial protocols, so as to achieve access control of different area boundaries in industrial control scenarios, or logical isolation between different business systems in the same area, increasing......

Security isolation and information import device
Used for secure data collection and physical isolation applications at the network boundary of industrial control systems, the product architecture mainly consists of three parts: internal network host system, external network host system, and isolation exchange.

WEB Application Firewall
WEB application firewall mainly provides security protection for web services. By collecting web access data and using professional protection engines for data detection, it can achieve conventional protection such as web protection, DDoS protection, intrusion protection, and webpage tamper resistance.

SVSS
Network Vulnerability Scanning and Management System
Vulnerability scanning products integrate multiple inspection capabilities, allowing for in-depth scanning of mainstream operating systems, web sites/applications, database systems, network devices, and various common applications......

Desert Fox Second Generation
Ensure secure transmission of cross domain data in the network
The second generation of edge computing gateway, front-end dynamometer diagnostic fluid metering equipment.
Adhering to high industrial standards and possessing excellent environmental adaptability. It can operate...
Adhering to high industrial standards and possessing excellent environmental adaptability. It can operate...

A front-end micro computing center with AI computing power.
Based on the edge layer of the industrial Internet platform, it is elaborately developed and adopts advanced embedded development technology to...
Based on the edge layer of the industrial Internet platform, it is elaborately developed and adopts advanced embedded development technology to...
Edge computing Gateway
GCT-X1130P

Dynamometer
three-phase electric parameter version
Using electrical parameters to automatically calculate indicator diagrams, convenient deployment, and low maintenance costs.
This product relies on advanced artificial intelligence and data mining technology to build an intelligent...
This product relies on advanced artificial intelligence and data mining technology to build an intelligent...



